Danny Yuxing Huang
,
Ph.D.
-
Assistant Professor

Danny Y. Huang is broadly interested in the following research areas:
- health, AI/ML, privacy: see RouterSense (passive patient monitoring with just network traffic)
- helping victims of tech-enabled abuse: e.g., improving large language models and building tools to detect hidden devices (such as IoT Inspector)
Before joining NYU, he was a postdoctoral fellow at Princeton University. He obtained a Ph.D. in Computer Science from University of California, San Diego, where he wrote a dissertation on using cryptocurrencies to study cyber-criminal activities. He graduated from Williams College (Massachusetts) with a BA in Computer Science.
Research News
NYU Tandon researchers adapt cybersecurity tool to monitor health through smartphone traffic
Borrowing a cybersecurity technique originally designed to catch malware, researchers at NYU Tandon School of Engineering have developed a new tool for monitoring human health without invasive wearables or unreliable self-reporting.
The method, dubbed RouterSense, passively analyzes encrypted network traffic on a person's smartphone or other digital device, tracking their digital behaviors to potentially shed light on conditions ranging from mental health struggles in young adults to early signs of Alzheimer's disease.
"Traffic patterns serve as proxies for digital biomarkers," explained Danny Huang, the project’s senior researcher. "Screen time indicates sleep patterns, texting frequency reflects social interaction, and app usage reveals productivity rhythms, for example."
Huang is an NYU Tandon assistant professor with appointments in the Electrical and Computer Engineering Department (ECE) and in the Computer Science and Engineering Department. He is also on the faculties of the NYU Center for Cybersecurity, the Center for Urban Science + Progress and the Center for Advanced Technology in Telecommunications.
Because the system only captures metadata — information about digital activity such as which apps are contacted rather than the activity itself — it never sees any actual content, keeping the person's messages, videos, and other online activity private. The approach works across a diverse set of devices: phones, tablets, PCs, whether they run on Apple, Android, or Windows systems.
The analysis RouterSense employs has long been used in cybersecurity to spot malware by detecting unusual communication patterns, such as a device suddenly sending data to an unknown server or making suspicious connection requests. RouterSense flips this, tracking an individual's normal smartphone patterns instead of flagging threats.
"For the past fifteen years, I've been using network traffic analysis to understand how cybercriminals behave," said Huang. "My prior work has demonstrated that network traffic analysis could reveal behavioral patterns at scale while protecting privacy, lessons we're now applying to healthcare."
The research, recently released as a preprint in the Journal of Medical Internet Research, promises notable benefits over current standard health monitoring. Self reports are often riddled with recall bias. Intrusive sensors and smartphone apps can drain batteries and make people acutely aware they're being monitored. RouterSense, by contrast, is low-cost, unobtrusive, and scalable to large populations.
In a proof-of-concept study, 38 NYU students installed a VPN app on their smartphones for two weeks, which routed all their internet traffic through a research server in an NYU lab for analysis. Of the 29 participants who contributed valid data, 27 remained active for more than five days, contributing an average of over 300 hours of monitored network traffic.
The system successfully captured daily activity rhythms and lifestyle patterns, including gaming habits and late-night food delivery use, demonstrating the feasibility of passive monitoring. Participants reported the system was easy to use with many noting they forgot they were being monitored.
"Our approach allows us to increase the bandwidth of patient monitoring for months to years," said lead author Rameen Mahmood, an NYU Tandon ECE Ph.D. candidate. "Network traffic analysis lets us do passive monitoring 24-7 over an extended period of time, which hasn't really been done before."
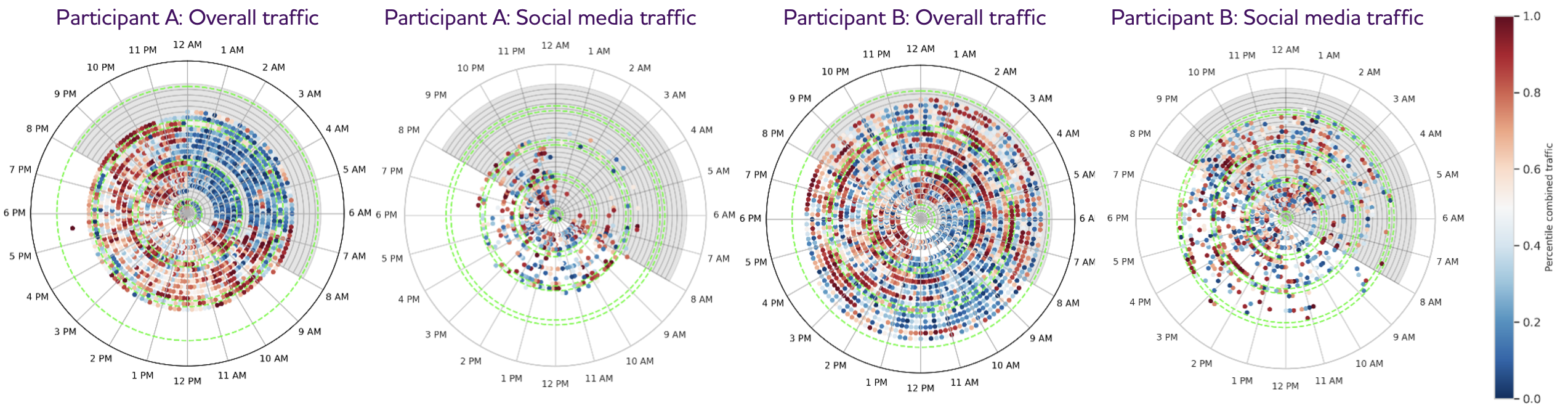
This visualization showcases data from two participants in the researchers' 14-day pilot study with 27 NYU students. Each ring represents a full day of passively monitored internet activity from their mobile phones. The dots illustrate 10-minute intervals of internet usage, with red indicating high activity and blue indicating low activity. Notice the clear difference in patterns: Participant A demonstrates a consistent daily routine, including a regular sleep schedule (the prominent blue region at night), while Participant B's activity is more varied. Click to view larger image.
The NYU Tandon study's success in demonstrating feasibility and acceptability has paved the way for clinical applications.
The researchers are now recruiting individuals with pre-Alzheimer's conditions for a 30-day monitoring study comparing their network traffic patterns with healthy controls, the crucial next step in determining whether RouterSense can detect early signs of cognitive decline.
Other areas the researchers plan to explore include digital behaviors related to mindless eating and brain development in younger populations.
In addition to Huang, Mahmood and Kaye, the paper’s authors are Donghan Hu and Annabelle David (NYU Tandon), Zachary Beattie (Oregon Health & Science University), Nabil Alshurafa (Northwestern University), Lou Haux (Max Planck Institute for Human Development), Josiah Hester (Georgia Institute of Technology), Andrew Kiselica (University of Georgia), Shinan Liu (University of Hong Kong), and Chenxi Qiu and Chao-Yi Wu (Harvard Medical School).
NYU Tandon researchers develop simple, low-cost method to detect GPS trackers hidden in vehicles, empowering cyberstalking victims
A team of researchers at NYU Tandon School of Engineering has developed a novel method to detect hidden GPS tracking devices in vehicles, offering new hope to victims of technology-enabled domestic abuse.
Overseen by NYU Tandon assistant professor Danny Y. Huang, the research addresses a growing problem: abusers secretly placing GPS trackers in their partners' or ex-partners' vehicles to monitor their movements. Traditionally, detecting these devices has been difficult and expensive, leaving many victims vulnerable to continued surveillance.
"The tech industry has created many tools that can be repurposed for cyberstalking, but has invested far less in technologies that protect privacy," said Huang. “We believe this innovation has the potential to significantly empower victims of domestic abuse by providing them with a readily accessible way to regain their privacy and safety."
Huang holds appointments in both the Electrical & Computer Engineering and Computer Science & Engineering departments. He is also a member of NYU Center for Cybersecurity, NYU Tandon's Center for Urban Science + Progress, and Center for Advanced Technology in Telecommunications.
"GPS tracking in domestic abuse situations is unfortunately common," said Moshe (Mo) Satt, a Ph.D. candidate working under Huang who is the lead author on the research paper that he will present at USENIX VehicleSec '25, a major cybersecurity conference, in August 2025. Satt is the Chief Information Security Officer (CISO) at the NYC Department of Sanitation and teaches several cybersecurity courses at the graduate and undergraduate levels as an NYU Tandon adjunct faculty member. "We wanted to develop a tool to combat it that is inexpensive and potentially very user-friendly."
The team's innovative approach relies on tinySA, a $150 palm-sized spectrum analyzer typically used by amateur radio enthusiasts for testing antennas and debugging wireless equipment.
Using this commercially-available device, the researchers developed a specialized algorithm that distinguishes weak tracker signals amid cellular transmission noise by monitoring LTE IoT uplink frequency bands. This approach — the first to reliably detect concealed 4G LTE IoT cellular GPS vehicle trackers using affordable equipment — isolates signals sent from concealed devices to nearby cell towers, solving technical challenges in determining which frequencies to scan, interpreting results, and filtering false positives.
For victims, the setup can potentially be used as a mobile detection system while driving. If the user observes regular signal peaks on the tinySA during or after a drive, they can likely identify the presence of a cellular GPS tracker without requiring technical expertise. The setup could detect hidden GPS tracker signals within a range of up to three feet, according to the study.
The research addresses a significant public safety concern affecting approximately 13.5 million stalking victims annually in the United States, 80 percent experiencing technological stalking. In some cases, this surveillance has led to violent attacks.
The researchers are developing several pathways to real-world implementation, including smartphone integration, automated "black box" detection systems that could notify the user if a tracker is detected, partnerships with abuse support organizations, and a mobile detection service model similar to roadside assistance.
In addition to Satt and Huang, the paper’s authors are Donghan Hu, a NYU Tandon postdoc working under Huang, and NYU Tandon Phd candidate Patrick Zielinski.
This research was made possible through funding from the NYU Center for Cybersecurity, NYU mLab, and NYU Tandon School of Engineering. Additional support was provided by the ARDC (Amateur Radio Digital Communications), ARRL (American Radio Relay League), Cornell Tech CETA (Clinic to End Tech Abuse), KAIST System Security lab, NYU OSIRIS, and NYU Tandon UGSRP (Undergraduate Summer Research Program).
Satt, Moshe & Hu, Donghan & Zielinski, Patrick & Huang, Danny. (2025). You Can Drive But You Cannot Hide: Detection of Hidden Cellular GPS Vehicle Trackers.
New research reveals alarming privacy and security threats in Smart Homes
An international team of researchers, led by IMDEA Networks and Northeastern University in collaboration with NYU Tandon School of Engineering, Universidad Carlos III de Madrid, IMDEA Software, University of Calgary, and the International Computer Science Institute, has unveiled groundbreaking findings on the security and privacy challenges posed by the ever-growing prevalence of opaque and technically complex Internet of Things (IoT) devices in smart homes.
Smart Homes: Trusted and Secure Environments?
Smart homes are becoming increasingly interconnected, comprising an array of consumer-oriented IoT devices ranging from smartphones and smart TVs to virtual assistants and CCTV cameras. These devices have cameras, microphones, and other ways of sensing what is happening in our most private spaces — our homes.
An important question is: can we trust that these devices in our homes are safely handling and protecting the sensitive data they have access to?
“When we think of what happens between the walls of our homes, we think of it as a trusted, private place. In reality, we find that smart devices in our homes are piercing that veil of trust and privacy — in ways that allow nearly any company to learn what devices are in your home, to know when you are home, and learn where your home is. These behaviours are generally not disclosed to consumers, and there is a need for better protections in the home,” said David Choffnes, Associate Professor of Computer Science and Executive Director of the Cybersecurity and Privacy Institute at Northeastern University.
The research team's extensive study, titled "In the Room Where It Happens: Characterizing Local Communication and Threats in Smart Homes," was presented this week at the ACM Internet Measurement Conference (ACM IMC'23) in Montreal (Canada).
The paper delves for the first time into the intricacies of local network interactions between 93 IoT devices and mobile apps, revealing a plethora of previously undisclosed security and privacy concerns with actual real-world implications.
While most users typically view local networks as a trusted and safe environment, the study's findings illuminate new threats associated with the inadvertent exposure of sensitive data by IoT devices within local networks using standard protocols such as UPnP or mDNS.
These threats include the exposure of unique device names, UUIDs, and even household geolocation data, all of which can be harvested by companies involved in surveillance capitalism without user awareness.
According to Vijay Prakash, PhD student from NYU Tandon who co-authored the paper, "analyzing the data collected by IoT Inspector, we found evidence of IoT devices inadvertently exposing at least one PII (Personally Identifiable Information), like unique hardware address (MAC), UUID, or unique device names, in thousands of real world smart homes. Any single PII is useful for identifying a household, but combining all three of them together makes a house very unique and easily identifiable. For comparison, if a person is fingerprinted using the simplest browser fingerprinting technique, they are as unique as one in 1,500 people. If a smart home with all three types of identifiers is fingerprinted, it is as unique as one in 1.12 million smart homes."
These local network protocols can be employed as side-channels to access data that is supposedly protected by several mobile app permissions such as household locations.
“A side channel is a sneaky way of indirectly accessing sensitive data. For example, Android app developers are supposed to request and obtain users’ consent to access data like geolocation. However, we have shown that certain spyware apps and advertising companies do abuse local network protocols to silently access such sensitive information without any user awareness. All they have to do is kindly ask for it to other IoT devices deployed in the local network using standard protocols like UPnP,” said Narseo Vallina-Rodriguez, Associate Research Professor of IMDEA Networks and co-founder of AppCensus.
“Our study shows that the local network protocols used by IoT devices are not sufficiently protected and expose sensitive information about the home and our use of the devices. This information is being collected in an opaque way and makes it easier to create profiles of our habits or socioeconomic level,” adds Juan Tapiador, professor at UC3M.
The Wider Implications
The impact of this research extends far beyond academia. The findings underscore the imperative for manufacturers, software developers, IoT and mobile platform operators, and policymakers to take action to enhance the privacy and security guarantees of smart home devices and households. The research team responsibly disclosed these issues to vulnerable IoT device vendors and to Google's Android Security Team, already triggering security improvements in some of these products.
About IMDEA Networks: IMDEA Networks is a non-profit, independent research institute located in Madrid (Spain). Its multinational research team conducts cutting-edge fundamental research in the fields of computer and communication networks to develop future network principles and technologies; designing and creating today the networks of tomorrow.
About Northeastern University: Founded in 1898, Northeastern is a global research university and the recognized leader in experience-driven lifelong learning. Our world-renowned experiential approach empowers our students, faculty, alumni, and partners to create impact far beyond the confines of discipline, degree, and campus.
About NYU Tandon School of Engineering: The NYU Tandon School of Engineering is home to a community of renowned faculty, undergraduate and graduate students united in a mission to understand and create technology that powers cities, enables worldwide communication, fights climate change, and builds healthier, safer, and more equitable real and digital worlds. NYU Tandon dates back to 1854 and is a vital part of New York University and its unparalleled global network.
About UC3M: The Universidad Carlos III de Madrid (UC3M) is a Spanish public university that excels in research, teaching and innovation. It is among the best universities in the world in the QS World University Rankings 2024 and among the best universities for the employability of its graduates, according to the latest edition of the Times Higher Education (THE) Global University Employability Ranking.
About IMDEA Software: The IMDEA Software Institute is a non-profit, independent research institute promoted by the Madrid Regional Government to perform research of excellence and technology transfer in the methods, languages, and tools that will allow the cost-effective development of software products with sophisticated functionality and high quality.
About University of Calgary: UCalgary is Canada’s entrepreneurial university, located in Canada’s most enterprising city. It is a top research university and one of the highest-ranked universities of its age. Founded in 1966, its 35,000 students experience an innovative learning environment, made rich by research, hands-on experiences and entrepreneurial thinking. It is Canada’s leader in the creation of start-ups. For more information, visit ucalgary.ca.
About International Computer Science Institute: ICSI is an independent non-profit research institute affiliated with the University of California, Berkeley. With a focus on scientific excellence and social impact, ICSI transcends disciplinary boundaries in computing and data sciences and collaborates internationally and across sectors to inspire breakthroughs.
Citation:
Aniketh Girish, Tianrui Hu, Vijay Prakash, Daniel J. Dubois, Srdjan Matic, Danny Yuxing Huang, Serge Egelman, Joel Reardon, Juan Tapiador, David Choffnes, and Narseo Vallina-Rodriguez. 2023. In the Room Where It Happens: Characterizing Local Communication and Threats in Smart Homes. In Proceedings of the 2023 ACM on Internet Measurement Conference (IMC '23). Association for Computing Machinery, New York, NY, USA, 437–456. https://doi.org/10.1145/3618257.3624830